Difference between revisions of "Internet Security"
From MgmtWiki
(→Context) |
(→Context) |
||
| Line 10: | Line 10: | ||
# Bad actors attacking service providers. | # Bad actors attacking service providers. | ||
| − | There are two interfaces of interest, (1) at the user's agent, and (2) at the provider endpoint access to the internet. | + | * There are two interfaces of interest, (1) at the user's agent, and (2) at the provider endpoint access to the internet. |
| + | * There is one source of trust of interest: a list of trusted service providers in either the user head or in the user's agent. | ||
[[File:InternetSecurity.png]] | [[File:InternetSecurity.png]] | ||
Revision as of 15:00, 17 September 2021
Full Title or Meme
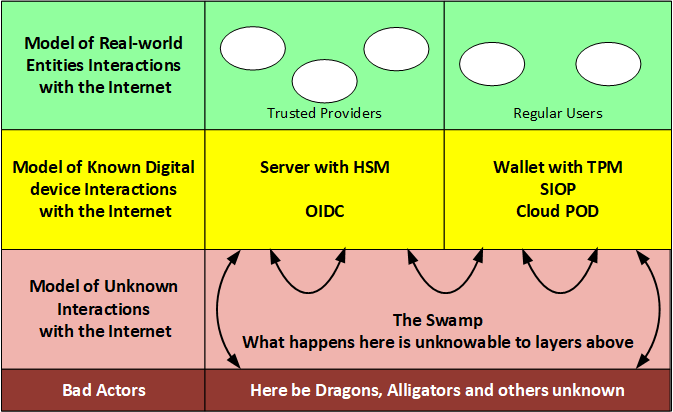
Internet Security appears to be an oxymoron as a network of networks could not be expected to harbor any underlying security model. So what ever security is to exist will need to be layered over the internet.
Context
While the Internet may appear to be just a swamp of bad actors, as shown below, we can discuss security for two broad categories of real-world actors, the service providers and the human users. The follows graphic shows those two real-world actors, together with their digital internet manifestations and the interactions among the actors.
- User to user
- User to Trusted Service Provider
- Service Prover to Service Provider
- Bad actor attacking users
- Bad actors attacking service providers.
- There are two interfaces of interest, (1) at the user's agent, and (2) at the provider endpoint access to the internet.
- There is one source of trust of interest: a list of trusted service providers in either the user head or in the user's agent.
- Also see the wiki page on Internet Bill of Rights