Difference between revisions of "Internet Security"
(→Context) |
(→Context) |
||
| Line 5: | Line 5: | ||
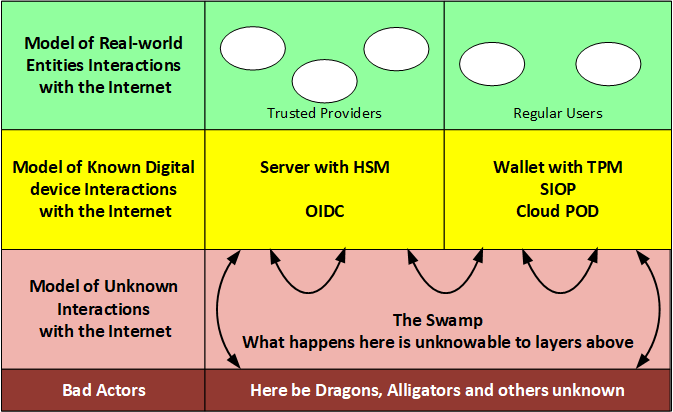
While the Internet may appear to be just a swamp of bad actors, as shown below, we can discuss security for two broad categories of real-world actors, the service providers and the human users. The follows graphic shows those two real-world actors, together with their digital internet manifestations and the interactions among the actors. | While the Internet may appear to be just a swamp of bad actors, as shown below, we can discuss security for two broad categories of real-world actors, the service providers and the human users. The follows graphic shows those two real-world actors, together with their digital internet manifestations and the interactions among the actors. | ||
# Human user to user -This particular path is almost never used in 2020. One good experience shows why users might like to increase its use is [https://na01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fwww.swissinfo.ch%2Feng%2Fprotonmail-scandal-tarnishes-swiss-privacy-reputation-%2F46952640&data=04%7C01%7C%7C1f2842848b58434628a808d97ab6a5c1%7C84df9e7fe9f640afb435aaaaaaaaaaaa%7C1%7C0%7C637675747145373177%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C1000&sdata=kuvP3Oh4tHMuf%2F5MiKHTxqn98HRssJAuDGfwelXM%2BlI%3D&reserved=0 the case of Proton Mail shared the IP address of one of its users as part of a French investigation that led to the arrest of climate activists.] The exact opposite behavior as the privacy they promised at their inception and the very activity for which Phil Zimmermann created PGP. | # Human user to user -This particular path is almost never used in 2020. One good experience shows why users might like to increase its use is [https://na01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fwww.swissinfo.ch%2Feng%2Fprotonmail-scandal-tarnishes-swiss-privacy-reputation-%2F46952640&data=04%7C01%7C%7C1f2842848b58434628a808d97ab6a5c1%7C84df9e7fe9f640afb435aaaaaaaaaaaa%7C1%7C0%7C637675747145373177%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C1000&sdata=kuvP3Oh4tHMuf%2F5MiKHTxqn98HRssJAuDGfwelXM%2BlI%3D&reserved=0 the case of Proton Mail shared the IP address of one of its users as part of a French investigation that led to the arrest of climate activists.] The exact opposite behavior as the privacy they promised at their inception and the very activity for which Phil Zimmermann created PGP. | ||
| − | # Human user to Trusted Service Provider | + | # Human user to Trusted Service Provider which should be the only connection that use agents allow, if it were only possible to determine which providers were not bad actors. |
# Service Provider to Service Provider | # Service Provider to Service Provider | ||
# Bad actor attacking users | # Bad actor attacking users | ||
Revision as of 08:21, 18 September 2021
Contents
Full Title or Meme
Internet Security appears to be an oxymoron as a network of networks could not be expected to harbor any underlying security model. So what ever security is to exist will need to be layered over the internet.
Context
While the Internet may appear to be just a swamp of bad actors, as shown below, we can discuss security for two broad categories of real-world actors, the service providers and the human users. The follows graphic shows those two real-world actors, together with their digital internet manifestations and the interactions among the actors.
- Human user to user -This particular path is almost never used in 2020. One good experience shows why users might like to increase its use is the case of Proton Mail shared the IP address of one of its users as part of a French investigation that led to the arrest of climate activists. The exact opposite behavior as the privacy they promised at their inception and the very activity for which Phil Zimmermann created PGP.
- Human user to Trusted Service Provider which should be the only connection that use agents allow, if it were only possible to determine which providers were not bad actors.
- Service Provider to Service Provider
- Bad actor attacking users
- Bad actors attacking service providers.
- There are two interfaces of interest, (1) at the user's agent, and (2) at the provider endpoint access to the internet.
- There is one source of trust of interest: a list of trusted service providers either in the user head or in the user's agent.
- All security is inherent in the messages that are received from the swamp, so the structure and content of these messages, combined with the security of the digital devices, procedures and programs used by the real-world entities will be the entire determinate of the security of the site.
- Also see the wiki page on Internet Bill of Rights
Problems
The shear volume of devices, software and procedures used at any digital endpoint makes securing the entirety of the endpoint very difficult. Attempts to focus on the protocols or data structures used in the interchanges over the internet have proved to be inadequate to the task.
As a first step this site will focus on the security of the user devices, in particular with the mobile smartphone both as a platform as the apps that work on that platform operating together as a user agent. This can be combined later in the project with any service providers that directly focus on user agent functions.
The complexities that can be faced in securing the operation of a user agent is well exhibited in this Louisiana Wallet example which can both protect the mobile driver's license of the holder, but also act as a verifier of other's license as might be encountered if the holder were a gig worker that had to verify the age of the recipient of, for example, a delivery of wine to the household. In this case the physical location of both smartphones, and the reason for the request (delivery of alcoholic beverages) can be known by the issuer.
Solutions
The solution proposed here is a set of security requirements for user agents holding mobile credentials which could let to a set of software assurance criteria that should be developed to enable testing of the mobile platforms and the applications running on those platforms.
Security Profile
- HTTPS (TLS) is used throughout the interchange which will block attackers from examining the data transferred.
- User authentication credentials are well protected by the user agent.
- If the user agent stores authentication credentials (for example in a password manager) they are not release in plain text without strong authentication of the user's presence at the device.