Difference between revisions of "Identity Ecosystem"
(→Solutions) |
|||
| Line 23: | Line 23: | ||
* The [[Trust Registry]] will typically only have a data base of entities and attributes of those entities together with assurance data. | * The [[Trust Registry]] will typically only have a data base of entities and attributes of those entities together with assurance data. | ||
* The destination could be a physical venue or just an online resource. | * The destination could be a physical venue or just an online resource. | ||
| + | * Governance applies at a high level to both the Trust Registries and to the policy deployed. | ||
[[File:Id Ecosystem.png]] | [[File:Id Ecosystem.png]] | ||
| Line 31: | Line 32: | ||
[[Category:Glossary]] | [[Category:Glossary]] | ||
[[Category:Identity]] | [[Category:Identity]] | ||
| + | [[Category:Regulation]] | ||
Revision as of 10:19, 26 February 2022
Full Title or Meme
The Identity Ecosystem needs to be a user-centric online environment – a set of Technology Infrastructures, policies and agreed upon standards that securely supports transactions ranging from anonymous to fully-authenticated and from low to high value.
Context
The National Strategy for Trusted Identities in Cyberspace (NSTIC) describes a vision of the future – an Identity Ecosystem – where individuals, businesses and other organizations enjoy greater trust and security as they conduct sensitive transactions online.
Problems
Most of the problems relate to user acceptance, for example:
- Am I being tracked against my will?
- Is all of my privacy information available on the web somewhere?
- Why should I trust anything on the web at all?
The government has a variety of reasons to know about the population including:
- Taxation, that is why Caesar called for all the world to be registered and why William the Conquerer created the doomsday book.
- Social services from the government are only available to some part of the population and should only be supplied once to each applicant.
- Application of punitive laws.
- Public Health.
Solutions
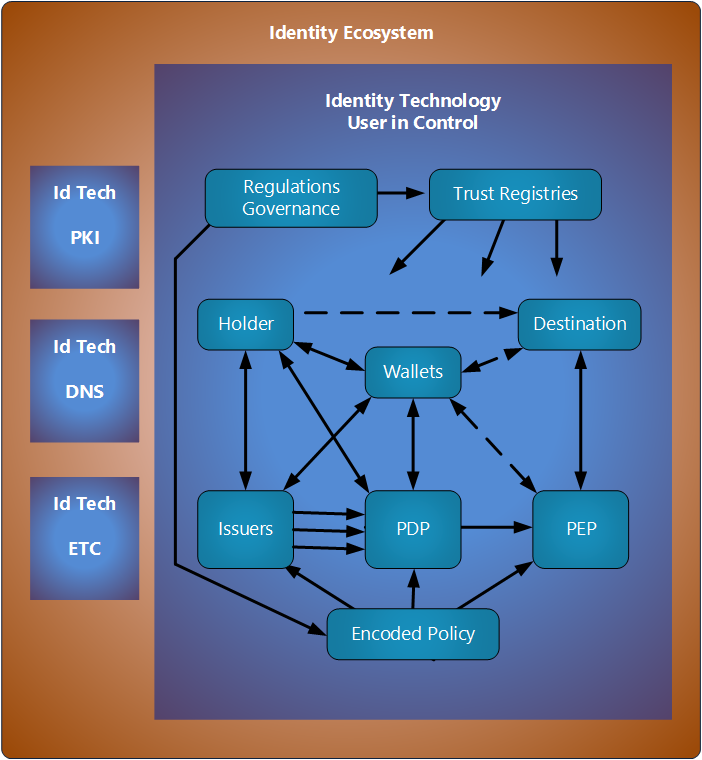
The following image puts the Identity Technology or Identity Infrastructure in conext of the various components that will likely exist.
- The Relying Party is shown here as two components: the Policy Definition Point and the Policy Execution Point.
- The policy is what tell the verifier in the RP what to accept. It is designed to be highly reactive to changes in policy that are to be expected as technologies and regulaltions evolve.
- The Trust Registry will typically only have a data base of entities and attributes of those entities together with assurance data.
- The destination could be a physical venue or just an online resource.
- Governance applies at a high level to both the Trust Registries and to the policy deployed.
References
- See the wiki page on Evolution for ways to encourage or discourage the continued growth of the Identity Ecosystem.