Difference between revisions of "Self-issued OpenID Picker"
(→Problems) |
(→Terms and Abbreviations) |
||
| (33 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
Self-issued Identifiers in an OpenID Connect Context where there is a large choice among OpenID providers.. | Self-issued Identifiers in an OpenID Connect Context where there is a large choice among OpenID providers.. | ||
| − | Also known as chooser or selector spec or as the Joint Authentication Management (JAM) specification. | + | Also known as chooser or selector spec or as the Joint Authentication Management (JAM) specification or as a [[Vendor Relationship Manager]]. |
===Goals=== | ===Goals=== | ||
| − | # Allow users the choice of which identifier to | + | # Allow users the choice of which identifier to use with a [[Relying Party]] in a world where thee number of options makes it hard for the [[Relying Party]] to list them all. |
# Allow users to easily navigate back to a [[Relying Party]] without having to remember their choice when they registered, which could easily be over a year in the past. | # Allow users to easily navigate back to a [[Relying Party]] without having to remember their choice when they registered, which could easily be over a year in the past. | ||
| + | |||
| + | ===Justification=== | ||
| + | There has never been much interest in [[User Experience]] among identifier standards developers. This wiki page attempts to address that. Some Commentary follows: | ||
| + | * David Cahdwick<blockquote>I think the whole direction of this Picker is misguided because it assumes that users will be knowledgeable about their numerous identifiers and will want to manage them. I don't believe that users will want to choose identifiers or know anything about them. I believe that users are interested in their electronic credentials (the equivalent of today’s plastic cards) and the identities that go with these. Users typically don't care a jot about what identifier is being used to cryptographically link their identity attributes to an identifier: transient identifiers are the best at protecting the user’s privacy and the user won't have any idea what the identifier is in any particular transaction. So the user will not be choosing identifiers as this draft assumes.</blockquote> | ||
| + | * Tom Jones<blockquote>I believe that there is a great deal of truth in David’s assertions about human’s desire for multiple identifier. The sad fact is i have ~100 of them today in spite of my desires to have none (they are typically called user names and each has their own lexical requirements). Without the help of a p/w manager i would not even be on atlassian at all. There are now ~100 DID methods. RPs will never to interested in supporting so many. How then to manage a world with ~100 digital identifiers per person? Doc Searls proposed a [[Vendor Relationship Manager]] (VRM) app, perhaps that would be a better word for what we are about?</blockquote> | ||
==Context== | ==Context== | ||
| Line 45: | Line 50: | ||
|RP || Relying Party, as used in [OIDC.Core] for any website the relies on claims produced by a CP for example an OP. | |RP || Relying Party, as used in [OIDC.Core] for any website the relies on claims produced by a CP for example an OP. | ||
|- | |- | ||
| − | | CP || Claims provider, Certificate Provider, Credential Provider, Credential Service Provider, etc. | + | | CP || Claims provider, Certificate Provider, Credential Provider, [[Credential Service Provider]] (CSP), etc. |
|- | |- | ||
| Identity Wallet || An application that is under the control and acts on behalf of the key credential holder. aka identity agent. can be a mobile app, browser extension/ plugin etc. | | Identity Wallet || An application that is under the control and acts on behalf of the key credential holder. aka identity agent. can be a mobile app, browser extension/ plugin etc. | ||
| Line 72: | Line 77: | ||
# Wallet | # Wallet | ||
# Identifier Friendly Name. | # Identifier Friendly Name. | ||
| − | Also sync can be performed at the high levels so that an individual can sync all devices and wallets, or a platform can sync all | + | Also sync can be performed at the high levels so that an individual can sync all devices and wallets, or a platform can sync all devices (and keystores) that share that platform. |
| + | |||
==Problems== | ==Problems== | ||
# As originally specified in section 7 of the [[OpenID Connect]] specification, there was a single end-point specified for the user. The implicit assumption here is that a user would only have a single wallet. That is not the way the world evolved. | # As originally specified in section 7 of the [[OpenID Connect]] specification, there was a single end-point specified for the user. The implicit assumption here is that a user would only have a single wallet. That is not the way the world evolved. | ||
# The [[Relying Party]]. RP cannot know all of the identifier providers at the user's disposal when the user first goes to the site. (Or returns anonymously.) | # The [[Relying Party]]. RP cannot know all of the identifier providers at the user's disposal when the user first goes to the site. (Or returns anonymously.) | ||
| − | # The user may not | + | # The user may not remember if they have already registered at the RP or which identifier they used when they last went to the RP. (The assumption is that there is on RP cookie on the users device. |
# The user may have a wide range of devices that they want to use as and where convenient to them. | # The user may have a wide range of devices that they want to use as and where convenient to them. | ||
# The current [Did.core] model does not address the user experience of having a number of identifiers that are completely unhelpful for user choice without some selection method they can understand. | # The current [Did.core] model does not address the user experience of having a number of identifiers that are completely unhelpful for user choice without some selection method they can understand. | ||
| + | |||
| + | ==User Experience== | ||
| + | This section addresses an optimal user experience with no consideration of where the picker resides or how is is implemented. The following are the expected steps to use the picker, or chooser as it is now known. | ||
| + | # User determines that they want to have one or more self-issued identifiers. | ||
| + | # User will have already selected at least a few credentials that they wish to store. We will assume these two as a base use case: | ||
| + | ## Driver's license | ||
| + | ## Health card in SHC format | ||
| + | # User will chose a smart phone and a wallet or user agent app to begin the process. This choice may be dictated by their required credentials. | ||
| + | # The wallet will give the user the option to enable one (or more) federated choices, perhaps based on the federation logo on their favorite web sites. The user will be given an option to list one or more of their personal self-issued identifiers. NOTE - all of the federation data can (optionally) be stored on the user's device and not on the the chooser site. (At a future time we might be able to include the sharing of that data on multiple devices owned by the user.) | ||
| + | # The next time the user goes to a web site where they have no active cookie, that site should list the particular federation logos that they have joined. | ||
| + | # The user clicks on the logo and one of several actions will occur: | ||
| + | ## The user as a single wallet with a single ID that is selected and the user is given the consent menu. | ||
| + | ## The user may have more than one ID on more than one wallet that are known to be part of that federation and so the user is give a choice as to which ID to use with this web site. | ||
| + | # The user consent dialog will be presented by the wallet with a list of the data types that were requested by the web site. (It's possible in the future that some of the data elements that are not required can be de-selected by the user as is required by, at least, the California privacy legislation). | ||
| + | # The user clicks "OK" and the user is connected to the web site as a fully registered user. | ||
| + | |||
| + | |||
| + | [[File:FrameworkChooser.png]] | ||
==Solutions== | ==Solutions== | ||
| Line 86: | Line 110: | ||
===Device Based=== | ===Device Based=== | ||
| − | * The ideal place for the picker is the | + | * The ideal place for the picker is the [[Password Manager]] in the browser, which can be loaded by the user, but that is painful at the start of 2021, so other solutions are needed in the short term. |
* The picker can be in a native app that assumes ownership of openid:// and sorts out the user choice on their own device. Unless a sharing solution were created, this would only work if the user had the app on every devices and initialized every device with their preferences. | * The picker can be in a native app that assumes ownership of openid:// and sorts out the user choice on their own device. Unless a sharing solution were created, this would only work if the user had the app on every devices and initialized every device with their preferences. | ||
| Line 277: | Line 301: | ||
Determine the verification method from the RP's DID Document that matches the kid of the SIOP Request. | Determine the verification method from the RP's DID Document that matches the kid of the SIOP Request. | ||
Verify the SIOP Request according to the verification method above. This step depends on the verification method in the authentication section in the DID Document and is out-of-scope of this specification. If the key pair that signed the SIOP Request refers to the same key as indicated by the verification method, then no additional verification has to be done as the SIOP validation will verify the signature of the JWS. | Verify the SIOP Request according to the verification method above. This step depends on the verification method in the authentication section in the DID Document and is out-of-scope of this specification. If the key pair that signed the SIOP Request refers to the same key as indicated by the verification method, then no additional verification has to be done as the SIOP validation will verify the signature of the JWS. | ||
| + | |||
| + | ===API for syncing picker data from the wallet to the picker=== | ||
| + | The need for a spec at this level seems helpful. No effort has been started by 2021-04-01 | ||
===UX Considerations=== | ===UX Considerations=== | ||
| − | The Picker will provide a UX with the user choices. This requires that a user (or user wallet) register their options the the picker. It is expected that such a registration API | + | The Picker will provide a UX with the user choices. This requires that a user (or user wallet) register their options the the picker. It is expected that such a registration API can be defined in some spec at a later time.. |
SIOP defines a custom URL scheme openid://. Mobile browsers would open the app that registered that scheme. Desktop browser extensions/ plugins have support for similar functionality. It is out of the scope of the spec under which circumstances a QR code will be rendered. One option will be to provide the QR code if the user is using the desktop browser, and no browser extension/ plugin is available. | SIOP defines a custom URL scheme openid://. Mobile browsers would open the app that registered that scheme. Desktop browser extensions/ plugins have support for similar functionality. It is out of the scope of the spec under which circumstances a QR code will be rendered. One option will be to provide the QR code if the user is using the desktop browser, and no browser extension/ plugin is available. | ||
| Line 325: | Line 352: | ||
===OIDC Considerations=== | ===OIDC Considerations=== | ||
| − | This | + | This work aims to be backward compatible with existing OIDC clients and OPs that implement the SIOP specification. Although the SIOP specification is part of the OIDC core specification, it is not widely adopted yet. One of the reasons was that not many apps existed that provided functionality we can find in Identity Wallets. Nevertheless, SIOP uses the same or similar request and response messages and should be easy to allow OIDC vendors to upgrade existing OIDC clients to support SIOP. |
==References== | ==References== | ||
<references /> | <references /> | ||
===Normative references=== | ===Normative references=== | ||
| − | [DID.Resolution] | + | * [DID.Resolution] Decentralized Identifier Resolution. Markus Sabadello; Dmitri Zagidulin. Credentials Community Group. Draft Community Group Report. URL: https://w3c-ccg.github.io/did-resolution/ |
| − | Decentralized Identifier Resolution. Markus Sabadello; Dmitri Zagidulin. Credentials Community Group. Draft Community Group Report. URL: https://w3c-ccg.github.io/did-resolution/ | + | * [draft-amringer-jose-chacha-00] Chacha derived AEAD algorithms in JSON Object Signing and Encryption (JOSE). G. Amringer. 2018. URL: https://tools.ietf.org/html/draft-amringer-jose-chacha-00 |
| − | [draft-amringer-jose-chacha-00] | + | * [draft-ietf-cose-webauthn-algorithms-03] COSE and JOSE Registrations for WebAuthn Algorithms. M. Jones. 2019. URL: https://tools.ietf.org/html/draft-ietf-cose-webauthn-algorithms-03 |
| − | Chacha derived AEAD algorithms in JSON Object Signing and Encryption (JOSE). G. Amringer. 2018. URL: https://tools.ietf.org/html/draft-amringer-jose-chacha-00 | + | * [OIDC.Core] OpenID Connect Core 1.0 incorporating errata set 1. N. Sakimura; J. Bradley; M. Jones; B. de Medeiros; C. Mortimore. 2014. URL: https://openid.net/specs/openid-connect-core-1_0.html |
| − | [draft-ietf-cose-webauthn-algorithms-03] | + | * [OIDC.Registration] OpenID Connect Dynamic Client Registration 1.0 incorporating errata set 1. N. Sakimura; J. Bradley; M. Jones. 2014. URL: https://openid.net/specs/openid-connect-registration-1_0.html |
| − | COSE and JOSE Registrations for WebAuthn Algorithms. M. Jones. 2019. URL: https://tools.ietf.org/html/draft-ietf-cose-webauthn-algorithms-03 | + | * [RFC6749] The OAuth 2.0 Authorization Framework. D. Hardt, Ed.. IETF. October 2012. Proposed Standard. URL: https://tools.ietf.org/html/rfc6749 |
| − | [OIDC.Core] | + | * [RFC7516] JSON Web Encryption (JWE). M. Jones; J. Hildebrand. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7516 |
| − | OpenID Connect Core 1.0 incorporating errata set 1. N. Sakimura; J. Bradley; M. Jones; B. de Medeiros; C. Mortimore. 2014. URL: https://openid.net/specs/openid-connect-core-1_0.html | + | |
| − | [OIDC.Registration] | ||
| − | OpenID Connect Dynamic Client Registration 1.0 incorporating errata set 1. N. Sakimura; J. Bradley; M. Jones. 2014. URL: https://openid.net/specs/openid-connect-registration-1_0.html | ||
| − | [RFC6749] | ||
| − | The OAuth 2.0 Authorization Framework. D. Hardt, Ed.. IETF. October 2012. Proposed Standard. URL: https://tools.ietf.org/html/rfc6749 | ||
| − | [RFC7516] | ||
| − | JSON Web Encryption (JWE). M. Jones; J. Hildebrand. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7516 | ||
===Informative references=== | ===Informative references=== | ||
| − | * [https://identity.foundation/did-siop/ Self-Issued OpenID Connect Provider DID Profile] DIF Working Group Draft | + | * [https://iiw.idcommons.net/20A/_DID_chooser_for_SIOP Original DID chooser for SIOP from the IIW session] |
| − | + | * https://iiw.idcommons.net/20A/_DID_chooser_for_SIOP 20A/ DID chooser for SIOP] IIW 2021 How can a user get a meaningful choice about which identifier to use on a website? | |
| − | [OAuth2.FormPost] | + | * [https://docs.google.com/presentation/d/1QXc5-m6n4zlC8jFEIN1XZQ2DM-TFd6yXlo4ZNZVGDbg/edit#slide=id.gd2c45a9dcd_2_75 SIOP Chooser Topics] How can a person have a meaningful choice about which identifier to use with a new service? Jeremie Miller PING |
| − | + | * [https://identity.foundation/did-siop/ Self-Issued OpenID Connect Provider DID Profile] DIF Working Group Draft DID https://www.w3.org/TR/did-core/. Drummond Reed; Manu Sporny; Dave Longley; Christopher Allen; Ryan Grant; Markus Sabadello. Decentralized Identifier Working Group. Working Draft. URL: https://www.w3.org/TR/did-core/ | |
| − | *[OAuth2.ResponseTypes] | + | * [OAuth2.FormPost] OAuth 2.0 Form Post Response Mode. M. Jones; B. Campbell. 2015. URL: https://openid.net/specs/oauth-v2-form-post-response-mode-1_0.html |
| − | OAuth 2.0 Multiple Response Type Encoding Practices. B. de Medeiros, Ed.; M. Scurtescu; P. Tarjan; M. Jones. 2014. URL: https://openid.net/specs/oauth-v2-multiple-response-types-1_0.html | + | *[OAuth2.ResponseTypes] OAuth 2.0 Multiple Response Type Encoding Practices. B. de Medeiros, Ed.; M. Scurtescu; P. Tarjan; M. Jones. 2014. URL: https://openid.net/specs/oauth-v2-multiple-response-types-1_0.html |
| − | *[OIDC.CIBA] | + | *[OIDC.CIBA] OpenID Connect Client Initiated Backchannel Authentication Flow - Core 1.0 draft-02. G. Fernandez; F. Walter; A. Nennker; D. Tonge; B. Campbell. 2019. URL: https://openid.net/specs/openid-client-initiated-backchannel-authentication-core-1_0-ID1.html |
| − | OpenID Connect Client Initiated Backchannel Authentication Flow - Core 1.0 draft-02. G. Fernandez; F. Walter; A. Nennker; D. Tonge; B. Campbell. 2019. URL: https://openid.net/specs/openid-client-initiated-backchannel-authentication-core-1_0-ID1.html | + | * [RFC7515] JSON Web Signature (JWS). M. Jones; J. Bradley; N. Sakimura. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7515 |
| − | [RFC7515] | + | *[RFC7517] JSON Web Key (JWK). M. Jones. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7517 |
| − | JSON Web Signature (JWS). M. Jones; J. Bradley; N. Sakimura. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7515 | + | *[RFC7797] JSON Web Signature (JWS) Unencoded Payload Option. M. Jones. IETF. February 2016. Proposed Standard. URL: https://tools.ietf.org/html/rf |
| − | [RFC7517] | ||
| − | JSON Web Key (JWK). M. Jones. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7517 | ||
| − | [RFC7797] | ||
| − | JSON Web Signature (JWS) Unencoded Payload Option. M. Jones. IETF. February 2016. Proposed Standard. URL: https://tools.ietf.org/html/rf | ||
===Other Material=== | ===Other Material=== | ||
| Line 367: | Line 384: | ||
[[Category:Standard]] | [[Category:Standard]] | ||
[[Category:Identity]] | [[Category:Identity]] | ||
| + | [[Category:User Experience]] | ||
[[Category:Authentication]] | [[Category:Authentication]] | ||
[[Category:Security]] | [[Category:Security]] | ||
[[Category:Best Practice]] | [[Category:Best Practice]] | ||
Latest revision as of 09:46, 24 September 2024
Full Title
Self-issued Identifiers in an OpenID Connect Context where there is a large choice among OpenID providers..
Also known as chooser or selector spec or as the Joint Authentication Management (JAM) specification or as a Vendor Relationship Manager.
Goals
- Allow users the choice of which identifier to use with a Relying Party in a world where thee number of options makes it hard for the Relying Party to list them all.
- Allow users to easily navigate back to a Relying Party without having to remember their choice when they registered, which could easily be over a year in the past.
Justification
There has never been much interest in User Experience among identifier standards developers. This wiki page attempts to address that. Some Commentary follows:
- David Cahdwick
I think the whole direction of this Picker is misguided because it assumes that users will be knowledgeable about their numerous identifiers and will want to manage them. I don't believe that users will want to choose identifiers or know anything about them. I believe that users are interested in their electronic credentials (the equivalent of today’s plastic cards) and the identities that go with these. Users typically don't care a jot about what identifier is being used to cryptographically link their identity attributes to an identifier: transient identifiers are the best at protecting the user’s privacy and the user won't have any idea what the identifier is in any particular transaction. So the user will not be choosing identifiers as this draft assumes.
- Tom Jones
I believe that there is a great deal of truth in David’s assertions about human’s desire for multiple identifier. The sad fact is i have ~100 of them today in spite of my desires to have none (they are typically called user names and each has their own lexical requirements). Without the help of a p/w manager i would not even be on atlassian at all. There are now ~100 DID methods. RPs will never to interested in supporting so many. How then to manage a world with ~100 digital identifiers per person? Doc Searls proposed a Vendor Relationship Manager (VRM) app, perhaps that would be a better word for what we are about?
Context
- Report of a method to improve a sign in User Experience from an RP site for first time signin with a self-issued ID than they can get with, say, Google or FB.
- Report of a method to improve a sign in when the user returns to the same site.
In both cases the user is given a choice on a "Selection" menu where options are related to something the user knows, which should be the identifiers that the user has enabled.
Terms and Abbreviations
| Term | Description |
| User | An organic human being operating a computing device, typically a smartphone or laptop. |
| DID | Decentralized Identifier as per DID.Core[1] |
| DID Document | DID Document as per [DID.Core] |
| SIOP DID | Self-Issued OpenID Connect Provider DID profile. Refers to a specific flavor(s) of Verification Method used in the OIDC SIOP flow. |
| JWT | JSON Web Token as per [RFC7797] |
| JWE | JSON Web Encryption as per [RFC7516] |
| JWS | JSON Web Signature as per [RFC7515] |
| JWK | JSON Web Key as per [RFC7517] |
| JWKS | JWK Set as per [RFC7517] |
| OIDC | OpenID Connect as per [OIDC.Core] |
| OAuth client | Used synonymously with Relying Party (see RP) |
| OP | OpenID Provider as per [OIDC.Core] |
| SIOP | Self-Issued OpenID Provider as per [OIDC.Core] section 7. |
| RP | Relying Party, as used in [OIDC.Core] for any website the relies on claims produced by a CP for example an OP. |
| CP | Claims provider, Certificate Provider, Credential Provider, Credential Service Provider (CSP), etc. |
| Identity Wallet | An application that is under the control and acts on behalf of the key credential holder. aka identity agent. can be a mobile app, browser extension/ plugin etc. |
| DID AuthN | Refers to a method of proofing control over a DID for the purpose of authentication. |
| Verification Method | a more recent name for one instance of a DID AuthN |
| Trust Authority | A URL endpoint that contains the references that define, inter alia, the operation of the picker and of the wallets |
| Trusted Wallet | code trusted by one or more Trust Authorities to protect user secrets and perhaps to validate user presence. |
| Identity Wallet | An application that is under the control and acts on behalf of the key credential holder. aka identity agent. can be a mobile app, browser extension/ plugin etc. |
| JAM session | The period of time from when the user clicks on a link in the RP until the UI for the wallet is accepted by the user. |
More items, especially those related to the meaning of origin or site are on the wiki page PWA initiators.
Scope of Picker
There really is not any one location or scope of control that needs to be determined. A picker can be at one one of these levels of control.
- Family
- Individual
- Platform (Android, Apple, etc.)
- Device
- Wallet
- Identifier Friendly Name.
Also sync can be performed at the high levels so that an individual can sync all devices and wallets, or a platform can sync all devices (and keystores) that share that platform.
Problems
- As originally specified in section 7 of the OpenID Connect specification, there was a single end-point specified for the user. The implicit assumption here is that a user would only have a single wallet. That is not the way the world evolved.
- The Relying Party. RP cannot know all of the identifier providers at the user's disposal when the user first goes to the site. (Or returns anonymously.)
- The user may not remember if they have already registered at the RP or which identifier they used when they last went to the RP. (The assumption is that there is on RP cookie on the users device.
- The user may have a wide range of devices that they want to use as and where convenient to them.
- The current [Did.core] model does not address the user experience of having a number of identifiers that are completely unhelpful for user choice without some selection method they can understand.
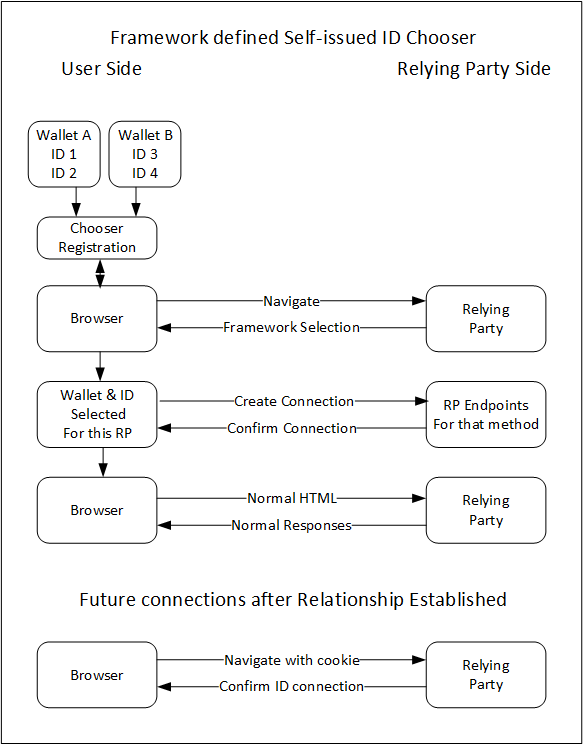
User Experience
This section addresses an optimal user experience with no consideration of where the picker resides or how is is implemented. The following are the expected steps to use the picker, or chooser as it is now known.
- User determines that they want to have one or more self-issued identifiers.
- User will have already selected at least a few credentials that they wish to store. We will assume these two as a base use case:
- Driver's license
- Health card in SHC format
- User will chose a smart phone and a wallet or user agent app to begin the process. This choice may be dictated by their required credentials.
- The wallet will give the user the option to enable one (or more) federated choices, perhaps based on the federation logo on their favorite web sites. The user will be given an option to list one or more of their personal self-issued identifiers. NOTE - all of the federation data can (optionally) be stored on the user's device and not on the the chooser site. (At a future time we might be able to include the sharing of that data on multiple devices owned by the user.)
- The next time the user goes to a web site where they have no active cookie, that site should list the particular federation logos that they have joined.
- The user clicks on the logo and one of several actions will occur:
- The user as a single wallet with a single ID that is selected and the user is given the consent menu.
- The user may have more than one ID on more than one wallet that are known to be part of that federation and so the user is give a choice as to which ID to use with this web site.
- The user consent dialog will be presented by the wallet with a list of the data types that were requested by the web site. (It's possible in the future that some of the data elements that are not required can be de-selected by the user as is required by, at least, the California privacy legislation).
- The user clicks "OK" and the user is connected to the web site as a fully registered user.
Solutions
- This document describes a picker which can intercept a AuthZ request flowing from an RP and help the user select the appropriate wallet and perhaps even the appropriate identifier.
- In all cases the user on a user agent (assumed here, without prejudice, to be a brewer) navigates to the Relying Party which displays one or more buttons that take the user to a picker which can be of any type located on any accessible site, include the device hosting the browser.
Device Based
- The ideal place for the picker is the Password Manager in the browser, which can be loaded by the user, but that is painful at the start of 2021, so other solutions are needed in the short term.
- The picker can be in a native app that assumes ownership of openid:// and sorts out the user choice on their own device. Unless a sharing solution were created, this would only work if the user had the app on every devices and initialized every device with their preferences.
Cloud Based
a cloud based solution is proposed for the sort term. The following discussion is based on a full could implementation but a web app solution would be a natural extension.
An everyday use case that the Decentralized Identity community identified is the sign-up or login with web applications. Nowadays, this is often achieved through social login schemes such as Google Sign-In. While the Decentralized Identity community has serious concerns about social login, the underlying protocol, OIDC, does not have these flaws by design. SIOP DID provides great potential by leveraging an Identity Wallet, e.g., as a smartphone app, on the web. This will increase and preserve the user’s privacy by preventing third-parties from having the ability to track which web applications a user is interacting with. SIOP focuses on the integration of Identity Wallets in the form of browser extensions/ plugins, or smartphone apps, it does not prevent implementers using the proposed flow in different scenarios as well, e.g., between two web services.
The main use case is to sign up with/ login (aka register) to an RP, i.e., website. It assumes the user operates a mobile or desktop browser or a browser-based app that can respond to SIOP requests.
The SIOP picker will eithe generate or pass trough the <SIOP Response> based on the specific DID method that the user choses. If required it can reconstitute or amend the request for transmission to the SIOP (wallet).The primary use case will install one or more identity wallets on the user smartphone.
This specification does not explicitly support any particular location for the picker. It is expected that both cloud-based and device based pickers will be enabled.
User Creates Choices
This is a series of actions that can involve:
- More that one device that protect user secrets in what is called here a Wallet.
- User may create any number of Identifiers on each wallet.
- User may wish to migrate or back-up the wallet on a number or devices.
- User may choose to include or exclude each Wallet' on any one of the user-controlled Wallets;
- No assumptions is made here about whether the devices are (1) smartphone (2) laptops, (3) user controlled servers, or (4) Wallet as a service. (Also called Mobile as a Service in the EU.
- Each Wallet is trusted on one ore more Trust Authorities.
- The RP gets to select the Trust Authorities that have the characteristics that will allow the RP to make a trust decsiion about users that seek to register with the RP.
Generate SIOP Request at the RP
The Redirect Request contains scope, response_type and client_id as query string parameters for backward compatibility with the OAuth2 specification [RFC6749]. response_type MUST be id_token and client_id MUST specify the callback URL of the RP (as per [OIDC.Core]). All other OIDC request parameters MUST be provided in an Request Object as per [OIDC.Core] which is encoded as a JWT. This enables the RP to authenticate against the SIOP using the RP's DID. The Request Object can be passed by value in the request request parameter, or by reference using the request_uri parameter.
The following are taken directly from the OIDC. It is not clear that the RP will know or even care whether the request is to be filled by a SIOP when a picker is used. It may not even be necessary for the picker to be limited to SIOP requests.
The following is a non-normative example HTTP 302 redirect response from the Client, which flows through the picker to the User Agent to make an Authentication Request to the Authorization Endpoint.
HTTP/1.1 302 Found Location: https://server.example.com/authorize? response_type=code &scope=openid%20profile%20email &client_id=s6BhdRkqt3 &state=af0ifjsldkj &redirect_uri=https%3A%2F%2Fclient.example.org%2Fcb
The following is the non-normative example request that would be redirected through the User Agent to the Authorization Server in response to the HTTP 302 redirect response by the Client above:
GET /authorize? response_type=code &scope=openid%20profile%20email &client_id=s6BhdRkqt3 &state=af0ifjsldkj &redirect_uri=https%3A%2F%2Fclient.example.org%2Fcb HTTP/1.1 Host: server.example.com
RP Meta-data
In contrast to other OIDC flows, e.g., Authorization Code Flow, RPs can provide client meta-data in the registration request parameter.
Request_object_signing_alg can be omitted. RPs implementing the DID AuthN profile MUST not use none for request_object_signing_alg.
There is no limitation placed on the ULR used by the client for identification. The JWKS MUST be provided in the jwks_uri or jwks entry of the registration parameter. Alternatively this can be handled by a DID doc.
RPs can decide to receive the SIOP Response encrypted. To enable encryption, the registration parameter MUST use id_token_encrypted_response_alg and id_token_encrypted_response_enc according to OIDC Client Metadata [OIDC.Registration].
Request Object The Request Object follows the OIDC specification, e.g., adding nonce, state, response_type, and client_id parameters.
The SIOP specification introduces additional rules for request parameters and claims in the Request Object:
Regular flow using a smartphone.
Request (Regular-device Flow) The request contains scope, response_type and client_id as query string parameters for backward compatibility with the OAuth2 specification [RFC6749]. response_type MUST be id_token and client_id MUST specify the callback URL of the RP (as per [OIDC.Core]). All other OIDC request parameters MUST be provided in an Request Object as per [OIDC.Core] which is encoded as a JWT. This enables the RP to authenticate against the SIOP using the RP's DID. The Request Object can be passed by value in the request request parameter, or by reference using the request_uri parameter.
The Request Object follows the OIDC specification, e.g., adding nonce, state, response_type, and client_id parameters.
This specification introduces additional rules for request parameters and claims in the Request Object:
REQUIRED. iss MAY contain the DID of the RP that can be resolved to a DID Document. The DID Document MUST contain a verification method in the authentication section, e.g., public key, that allows the SIOP to verify the Request Object. By default, the iss claim refers to the client_id but SIOP assumes that client_id is the callback URL of the RP. That is the reason why the DID is not encoded in the client_id. It is compliant with the OIDC specification to use different values for iss and client_id. REQUIRED. kid MUST be a DID URL referring to a verification method in the authentication section in the RP's DID Document, e.g., did:example:0xab#key1. The SIOP MUST be able to use that verification method to verify the Request Object directly or indirectly. Additionally, the referred JWKS in the registration parameter MUST contain an entry with the same kid. REQUIRED. scope MUST include did_authn to indicate the SIOP DID profile is used. REQUIRED. registration MUST be included in the Request Object REQUIRED. client_id MUST be repeated in the Request Object OPTIONAL. did_doc MUST contain the DID Document that corresponds to the DID in the iss claim. OPTIONAL. response_mode specifies how the response is returned to the callback URL by the SIOP. SIOP implementing this specification MAY set the response_mode to form_post. fragment is the default Response Mode. RPs MUST take into consideration the platform of the User-Agent when specifying this request parameter. OPTIONAL. response_context specifies whether the response should be returned to the callback URL in the context of an existing system browser session, or whether the response can be returned in a new/empty context (requested with a response_context of wallet). The default response_context is rp, indicating that the response should be submitted in the conext of the RP's existing system browser session.
The following is a non-normative example of the JWT header of a Request Object:
EXAMPLE 3
{
"alg": "ES256K",
"typ": "JWT",
"kid": "did:example:0xab#veri-key1"
} The following is a non-normative example of the JWT payload of a Request Object without requesting <SIOP DID Response> encryption:
EXAMPLE 4
{
"iss": "did:example:0xab",
"response_type": "id_token",
"client_id": "https://my.rp.com/cb",
"scope": "openid did_authn",
"state": "af0ifjsldkj",
"nonce": "n-0S6_WzA2Mj",
"response_mode" : "form_post",
"registration" : {
"jwks_uri" : "https://uniresolver.io/1.0/identifiers/did:example:0xab;transform-keys=jwks",
"id_token_signed_response_alg" : "ES256K"
}
}
The following is a non-normative example HTTP 302 redirect response by the RP, which triggers the User-Agent to make an SIOP DID Authentication Request using Request Object by value to the SIOP (with line wraps within values for display purposes only):
EXAMPLE 5
HTTP/1.1 302 Found Location: openid://? &client_id=https%3A%2F%2Frp.example.com%2Fcb &scope=openid%20did_authn &request=<JWT>
The following is a non-normative example HTTP 302 redirect response by the RP, which triggers the User-Agent to make an SIOP DID Authentication Request using Request Object by reference to the SIOP (with line wraps within values for display purposes only):
EXAMPLE 6
HTTP/1.1 302 Found Location: openid://? response_type=id_token &client_id=https%3A%2F%2Frp.example.com%2Fcb &scope=openid%20did_authn &request_uri=https%3A%2F%2Frp.example.com%2F90ce0b8a-a910-4dd0
See OAuth 2.0 Form Post Response Mode [OAuth2.FormPost] and OAuth 2.0 Multiple Response Type Encoding Practices [OAuth2.ResponseTypes] for more information about response_mode.
The following is a non-normative example of the JWT header of a Request Object:
EXAMPLE 7
{
"alg": "ES256K",
"typ": "JWT",
"kid": "did:example:0xab#veri-key1"
}
The following is a non-normative example of the JWT payload of a Request Object without requesting <SIOP Response> encryption:
EXAMPLE 8
{
"iss": "did:example:0xab",
"response_type": "id_token",
"client_id": "https://my.rp.com/cb",
"scope": "openid did_authn",
"state": "af0ifjsldkj",
"nonce": "n-0S6_WzA2Mj",
"response_mode" : "form_post",
"registration" : {
"jwks_uri" : "https://uniresolver.io/1.0/identifiers/did:example:0xab;transform-keys=jwks",
"id_token_signed_response_alg" : [ "ES256K", "EdDSA", "RS256" ]
}
}
Encryption JWE encryption MUST use Diffie-Hellman key agreement, i.e., algorithm ECDH-ES using the X25519 curve which uses direct key agreement with an ephemeral key. This means that a symmetric key is derived using Diffie-Hellman from the RP's public key and a randomly generated ephemeral private key. The corresponding ephemeral public key is included in the header of the JWE in the epk and the derived symmetric key is used to directly encrypt the JWT content. For symmetrically encrypting the content XChaCha20Poly1305 is used which has algorithm code XC20P.
The following is an example of the protected header of the resulting JWE:
EXAMPLE 9
{
"alg": "ECDH-ES",
"epk":
{
"kty": "OKP",
"crv":"X25519",
"x":"hSDwCYkwp1R0i33ctD73Wg2_Og0mOBr066SpjqqbTmo"
}
"enc": "XC20P",
"kid": "did:example:0xab#key-1"
}
Note that the kid above denotes the DID and key of the RP, i.e., this public key is the key used by the sender together with the ephemeral private key in order to derive the shared secret. For the encryption the 24 bytes nonce field in the XChaCha20 algorithm is used as the initialization vector. The authentication tag is the MAC computed by the Poly1305 function. It is 16 bytes long.
The message to be encrypted is the JWT of the id_token, including header and signature. The JWT is encoded via base64url before encryption.
For the final encoding of the JWE the JWE Compact Serialization outlined in [RFC7516] is used. The structure of the message is as follows:
EXAMPLE 10 BASE64URL(JWE Protected Header) || '.' || '.' || BASE64URL(JWE Initialization Vector) || '.' || BASE64URL(JWE Ciphertext) || '.' || BASE64URL(JWE Authentication Tag) Note the two '.' characters above which indicates that the encrypted key is empty since we are using direct key agreement.
Processing the SIOP Request at the Picker
The Picker MUST validate the <SIOP Request> by following the Self-Issued ID Token Validation rules as per [OIDC.Core]. NOTE The step described above ensures that the Request Object is verified according to the OIDC specification. This includes basic JWS verification.
If scope contains the did_authn scope, the receiving Picker or SIOP MUST further validate the SIOP Request as follows in no particular order:
If no did_doc is present, resolve the DID Document from the RP's DID specified in the iss request parameter. If did_doc is present, ensure this is a viable channel to exchange the RP's DID Document according to the applicable DID method. If jwks_uri is present, ensure that the DID in the jwks_uri matches the DID in the iss claim. Determine the verification method from the RP's DID Document that matches the kid of the SIOP Request. Verify the SIOP Request according to the verification method above. This step depends on the verification method in the authentication section in the DID Document and is out-of-scope of this specification. If the key pair that signed the SIOP Request refers to the same key as indicated by the verification method, then no additional verification has to be done as the SIOP validation will verify the signature of the JWS.
API for syncing picker data from the wallet to the picker
The need for a spec at this level seems helpful. No effort has been started by 2021-04-01
UX Considerations
The Picker will provide a UX with the user choices. This requires that a user (or user wallet) register their options the the picker. It is expected that such a registration API can be defined in some spec at a later time..
SIOP defines a custom URL scheme openid://. Mobile browsers would open the app that registered that scheme. Desktop browser extensions/ plugins have support for similar functionality. It is out of the scope of the spec under which circumstances a QR code will be rendered. One option will be to provide the QR code if the user is using the desktop browser, and no browser extension/ plugin is available.
On Android, the user can choose which app should open if multiple apps registered the same custom URL scheme. On iOS, the behavior is undefined. One approach would be to check if the user is on an iOS device and then, won't render the button if this is a concern. A fallback on iOS could be the use of custom mime types, but unusual UX has to be considered. Note, this issue is not specific to SIOP only but affects all apps using custom URL schemes. In case a QR Code is used where the user has to open the app first and has to scan the QR Code, this issue is mitigated.
Security Considerations
Threat: Interception of the Redirect URI If an attacker can cause the <SIOP Response> to be sent a URI under his control, he will directly get access to the fragment carrying the id_token.
This attack can be mitigated by hardening the RP, e.g., no support for the open redirector pattern.
Threat: Identity Token Leak in Browser History An attacker could obtain the <SIOP Response> from the browser's history.
This attack cannot be fully mitigated. It is RECOMMENDED to use short expiration times for id_token, and indicating that browsers should not cache the response.
Threat: Identity Token Leak to Third Party Scripts It is relatively common to use third-party scripts on RP pages, such as analytics tools, crash reporting. The author of the application may not be able to be fully aware of the entirety of the code running in the application. When a <SIOP Response> is returned in the fragment, it is visible to any third-party scripts on the page.
This attack could be mitigated by using trusted/ audited third party scripts on the RP's page, or browser-based app.
Countermeasures Use response_mode=form_post whenever possible to mitigate the risks described above. Under some circumstances, e.g., this will not be possible as such in the case of purely decentralized apps (dApp).
Threat: Session Fixation in Cross-Device Flow When the protocol begins on one device and ends on another, there is a risk that the cross-device transfer can be hijacked. For example, consider a flow that begins with the display of a QR code by the RP transfers to a mobile wallet when the user scans the QR code. In this scenario, an attacker can trick the user into scanning a QR code associated with a legitimate RP's sign-in request, thereby causing the user to authenticate within the context of the attacker's session.
Countermeasures Validate that the browser session in which the DID SIOP Response is submitted belongs to the same user as the browser session in which the DID SIOP Request was displayed. Even if these sessions are on different devices, the RP can take steps to ensure these belong to the same user (e.g., by checking whether an existing session exists or by asking the user to sign in through a non-SIOP means).
Additional Security Considerations
- Putting user information in a central location creates a rich source of data that attackers can target. Metamask performed similar function crytocurrency that created a paradigm that attackers could follow to acquire user trust maleciously.[2]
- The OWASP Foundation maintains a set of security recommendations and best practices for web applications, and it is RECOMMENDED to follow these best practices when creating an SIOP or RP based on this specification.
UX Considerations
- It is expected that each trust federation will create their own picker, although a federation of federations is a distinct possibility.
- The RP will need little change as the picker will appear to be a normal OIDC URL. It is expected that there will be additional text provided by the RP to inform the user as the the expectation on clicking a picker (federation) button.
- For Native apps the URL Schema redirect can be overridden the the last app to request access.
- For PWA (web apps) the URL is bound to the web site that installed the PWA, leading to exacerbations of the NASCAR logo problem.
- For Web App installations, TBD - complex
OIDC Considerations
This work aims to be backward compatible with existing OIDC clients and OPs that implement the SIOP specification. Although the SIOP specification is part of the OIDC core specification, it is not widely adopted yet. One of the reasons was that not many apps existed that provided functionality we can find in Identity Wallets. Nevertheless, SIOP uses the same or similar request and response messages and should be easy to allow OIDC vendors to upgrade existing OIDC clients to support SIOP.
References
- ↑ W3C, Decentralized Identifiers (DIDs) v1.0. https://www.w3.org/TR/did-core
- ↑ Datid Canellis, PSA: MetaMask reveals your Ethereum address to sites you visit, here’s how to hide it Hard Fork | The Next Web (2019-03-22) https://thenextweb.com/hardfork/2019/03/22/metamask-ethereum-privacy-address/
Normative references
- [DID.Resolution] Decentralized Identifier Resolution. Markus Sabadello; Dmitri Zagidulin. Credentials Community Group. Draft Community Group Report. URL: https://w3c-ccg.github.io/did-resolution/
- [draft-amringer-jose-chacha-00] Chacha derived AEAD algorithms in JSON Object Signing and Encryption (JOSE). G. Amringer. 2018. URL: https://tools.ietf.org/html/draft-amringer-jose-chacha-00
- [draft-ietf-cose-webauthn-algorithms-03] COSE and JOSE Registrations for WebAuthn Algorithms. M. Jones. 2019. URL: https://tools.ietf.org/html/draft-ietf-cose-webauthn-algorithms-03
- [OIDC.Core] OpenID Connect Core 1.0 incorporating errata set 1. N. Sakimura; J. Bradley; M. Jones; B. de Medeiros; C. Mortimore. 2014. URL: https://openid.net/specs/openid-connect-core-1_0.html
- [OIDC.Registration] OpenID Connect Dynamic Client Registration 1.0 incorporating errata set 1. N. Sakimura; J. Bradley; M. Jones. 2014. URL: https://openid.net/specs/openid-connect-registration-1_0.html
- [RFC6749] The OAuth 2.0 Authorization Framework. D. Hardt, Ed.. IETF. October 2012. Proposed Standard. URL: https://tools.ietf.org/html/rfc6749
- [RFC7516] JSON Web Encryption (JWE). M. Jones; J. Hildebrand. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7516
Informative references
- Original DID chooser for SIOP from the IIW session
- https://iiw.idcommons.net/20A/_DID_chooser_for_SIOP 20A/ DID chooser for SIOP] IIW 2021 How can a user get a meaningful choice about which identifier to use on a website?
- SIOP Chooser Topics How can a person have a meaningful choice about which identifier to use with a new service? Jeremie Miller PING
- Self-Issued OpenID Connect Provider DID Profile DIF Working Group Draft DID https://www.w3.org/TR/did-core/. Drummond Reed; Manu Sporny; Dave Longley; Christopher Allen; Ryan Grant; Markus Sabadello. Decentralized Identifier Working Group. Working Draft. URL: https://www.w3.org/TR/did-core/
- [OAuth2.FormPost] OAuth 2.0 Form Post Response Mode. M. Jones; B. Campbell. 2015. URL: https://openid.net/specs/oauth-v2-form-post-response-mode-1_0.html
- [OAuth2.ResponseTypes] OAuth 2.0 Multiple Response Type Encoding Practices. B. de Medeiros, Ed.; M. Scurtescu; P. Tarjan; M. Jones. 2014. URL: https://openid.net/specs/oauth-v2-multiple-response-types-1_0.html
- [OIDC.CIBA] OpenID Connect Client Initiated Backchannel Authentication Flow - Core 1.0 draft-02. G. Fernandez; F. Walter; A. Nennker; D. Tonge; B. Campbell. 2019. URL: https://openid.net/specs/openid-client-initiated-backchannel-authentication-core-1_0-ID1.html
- [RFC7515] JSON Web Signature (JWS). M. Jones; J. Bradley; N. Sakimura. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7515
- [RFC7517] JSON Web Key (JWK). M. Jones. IETF. May 2015. Proposed Standard. URL: https://tools.ietf.org/html/rfc7517
- [RFC7797] JSON Web Signature (JWS) Unencoded Payload Option. M. Jones. IETF. February 2016. Proposed Standard. URL: https://tools.ietf.org/html/rf
Other Material
- The use case User Agent in the Cloud explores the deployment of a picker and perhaps more for the user in the cloud.
- Alternative version on OpenID from Tom Jones
- parent folder for SIOP docs on OpenID.net