Difference between revisions of "Policy-Based Access Control"
(→Context) |
(→Evaluation of Policy) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 5: | Line 5: | ||
==Context== | ==Context== | ||
* This wiki applies specifically to policy expressed digitally in communications protocols; not that in human resources policies. | * This wiki applies specifically to policy expressed digitally in communications protocols; not that in human resources policies. | ||
| − | * The most common [[Attribute]]-Based Access Control language [[Policy Language | + | * The most common [[Attribute]]-Based Access Control language [[Policy Language#XACML|XACML]] expanded their scope in version 3.0 to include the description [[Policy-Based Access Control]] although policy statement was defined in earlier versions. |
===Existing Languages=== | ===Existing Languages=== | ||
| Line 44: | Line 44: | ||
===Evaluation of Policy=== | ===Evaluation of Policy=== | ||
* [https://aws.amazon.com/blogs/opensource/introducing-cedar-analysis-open-source-tools-for-verifying-authorization-policies/ Introducing Cedar Analysis: Open Source Tools for Verifying Authorization Policies] | * [https://aws.amazon.com/blogs/opensource/introducing-cedar-analysis-open-source-tools-for-verifying-authorization-policies/ Introducing Cedar Analysis: Open Source Tools for Verifying Authorization Policies] | ||
| + | * 2025-07-16 [https://medium.com/janssen-project-feed/using-cedar-to-modernize-authz-in-a-node-js-backend-d204fb4dc55e Using Cedar to Modernize Authz in A Node.js Backend] Janssen Project Feed | ||
==References== | ==References== | ||
Latest revision as of 14:04, 16 July 2025
Contents
Full Title or Meme
Policy-Based Access Control or PBAC is any system where Access is mediated by Access Tokens that are evaluated by a digital policy language and policy control engine.
Context
- This wiki applies specifically to policy expressed digitally in communications protocols; not that in human resources policies.
- The most common Attribute-Based Access Control language XACML expanded their scope in version 3.0 to include the description Policy-Based Access Control although policy statement was defined in earlier versions.
Existing Languages
These are all written by geeks, and for geeks. What is needed is some policy that works in a real-world user journey. In other words, the user needs to be able to understand what is expected and when.
For more background see the page Policy Language.
Cardea
They have been working with the government of Aruba and come up with the most through look at the problem in 2022. The have picked the unfortunate name of Machine Readable Governance, but it really is a description of the government's policy. Unfortunately, it might change daily and does not meet the requirement of testing by the user and remaining valid for even the duration of a flight from the US to the island.
- Machine Readable Governance. A JWT with a mishmash of different levels of abstraction from human readable questions to access policy.
- Cardea on GitHub.
Solution
This wiki page is interested in the machine-readable policy language and how it can be applied to access control.
Policy Distribution
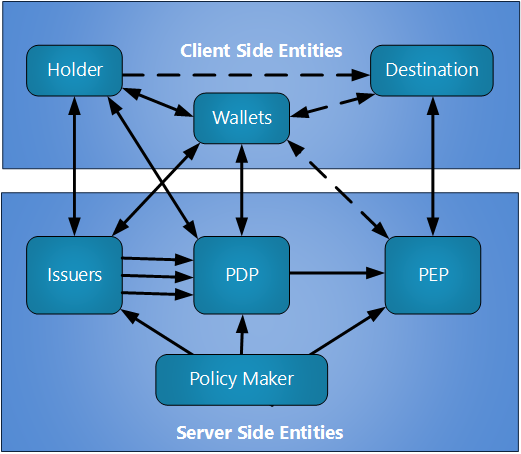
Policy can be made at the government level or by a resource owner. When a user is attempting to access some digital resource or some real-world venue, it is typically important for the user to know if they have the credentials to achieve their objective in advance. For example, in the Biometric Pre-Check use case the traveler (denoted as the holder in the image below) is expected to be able to determine if they can pass through the check-in line before they even leave home for the airport. The solid lines in the figure below are data transfers. The dotted lines are physical presentations, not all of which are required in every case.
User Experience
It is expected as the Mobile Driver's License become commonly available that identity and health credentials will generally be available in the holder's Smartphone.
Including the Policy with the Token
The mechanism for associating a Cedar policy with an access token and using it for access control decisions has started working as intended. The basic idea is to embed a Cedar policy into a RAR object (RFC 9396: OAuth 2.0 Rich Authorization Requests). With this mechanism, it's possible to generate access tokens with very specific permissions. For example, an access token that can only read the status of the Shared Signals Framework stream 'stream123' can be issued with the following 'authorization_details':
Evaluation of Policy
- Introducing Cedar Analysis: Open Source Tools for Verifying Authorization Policies
- 2025-07-16 Using Cedar to Modernize Authz in A Node.js Backend Janssen Project Feed
References
Other Material
- For policy applied at the web page origin see the wiki page on Content Security Policy.
- For more information see the wiki page on Policy Language.