Identity Ecosystem
Full Title or Meme
The Identity Ecosystem needs to be a user-centric online environment – a set of Technology Infrastructures, policies and agreed upon standards that securely supports transactions ranging from anonymous to fully-authenticated and from low to high value.
Context
The National Strategy for Trusted Identities in Cyberspace (NSTIC) describes a vision of the future – an Identity Ecosystem – where individuals, businesses and other organizations enjoy greater trust and security as they conduct sensitive transactions online.
Problems
Most of the problems relate to user acceptance, for example:
- Am I being tracked against my will?
- Is all of my privacy information available on the web somewhere?
- Why should I trust anything on the web at all?
- Can I know, in advance, whether I have the credentials I need to get to my destination.
The government has a variety of reasons to know about the population including:
- Taxation, that is why Caesar called for all the world to be registered and why William the Conqueror created the doomsday book.
- Social services from the government are only available to some part of the population and should only be supplied once to each applicant.
- Application of punitive laws.
- Public Health.
Liability seems to be a MAJOR stumbling block. Everyone is trying to avoid it, or mitigate it or make money from it.
- If you are not a sovereign state, then touching user private data is a mine field that most companies are either avoiding or seeking the least damaging path through it.
- Finding a private enterprise that will honor user wishes ahead of their own self-interest is an enduring issue ever since Milton Freedman told them that morality was not their problem.
Solutions
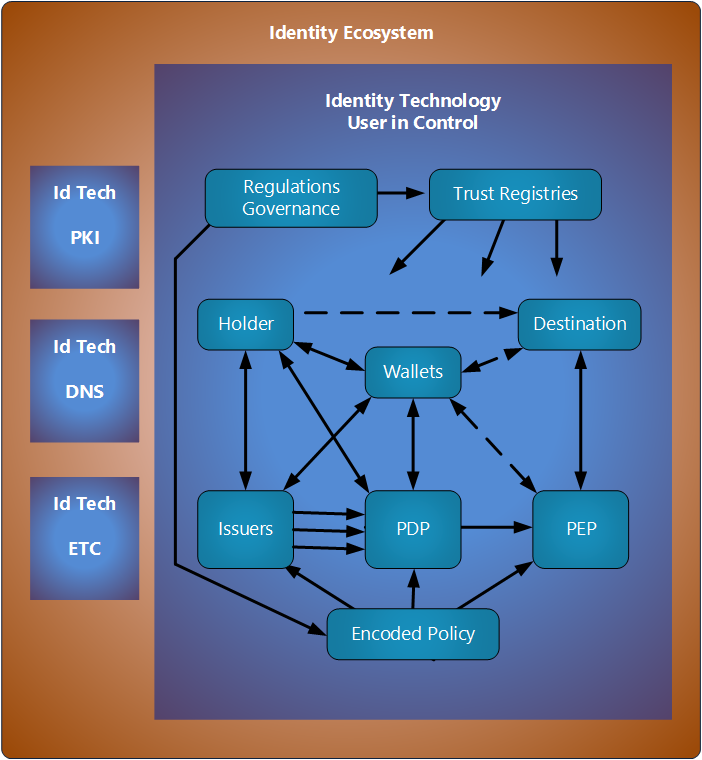
The following image puts the Identity Technology or Identity Infrastructure in conext of the various components that will likely exist.
- The Relying Party is shown here as two components: the Policy Definition Point and the Policy Execution Point.
- The policy is what tell the verifier in the RP what to accept. It is designed to be highly reactive to changes in policy that are to be expected as technologies and regulaltions evolve.
- The Trust Registry will typically only have a data base of entities and attributes of those entities together with assurance data.
- The destination could be a physical venue or just an online resource.
- Governance applies at a high level to both the Trust Registries and to the policy deployed.
Other Efforts
- Principles for Digital Trust Networks (2022-02-15) IIF = Institute for International Finance. (nb. The involvement of the OIDF might be overstated here.)
The Open Digital Trust Initiative of the IIF together with the Open ID Foundation has finalized Principles for Digital Trust Networks, identifying at a high level the ‘rules of the road’ that Digital Trust Networks should adopt in order to incentivize a high level of digital trust, user centricity and low cost, while ensuring that these networks are economically viable and the role of Verification Service Provider is adequately rewarded and realistically protected from a liability perspective. The broad vision is for Digital Trust Networks to comprise a set of participants, including both Users (who are also individual Data Subjects for individual data protection purposes in many cases), Verification Service Providers and Relying Parties. There is also scope for other types of intermediaries to be defined by the Network rules.
- Legal aspects of Identity Management and Trust Services 2018 Anna Joubin-Bret Secretary UNCITRAL (Thie UNCITRAL effort has been stumbling along for years. The primary issue seems to be liability. No one want any of that.)
References
- See the wiki page on Evolution for ways to encourage or discourage the continued growth of the Identity Ecosystem.