Difference between revisions of "Verifier"
From MgmtWiki
(→Context) |
(→Solutions) |
||
| Line 14: | Line 14: | ||
==Solutions== | ==Solutions== | ||
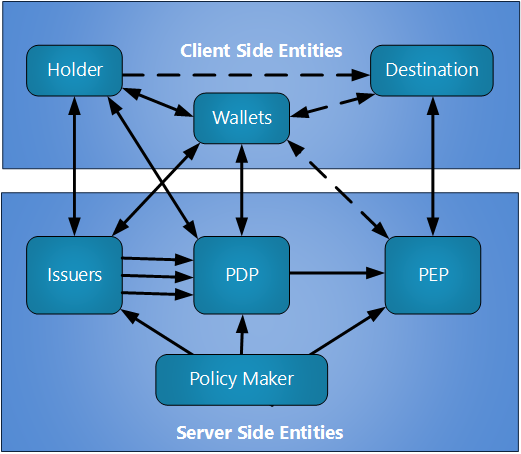
For this wiki we break the [[Verifier]] into two roles from SAML: | For this wiki we break the [[Verifier]] into two roles from SAML: | ||
| + | # Holder = a real-world entity that has a collection of centennials in a digital format contained in a digital wallet. | ||
# PDP = policy definition point may act as a [[Credential Aggregation]] process that accepts a collection of sources and produces a ticket for the holder that still needs to be bound to the person presenting the ticket. | # PDP = policy definition point may act as a [[Credential Aggregation]] process that accepts a collection of sources and produces a ticket for the holder that still needs to be bound to the person presenting the ticket. | ||
# PEP = policy enforcement point accepts sources of attributes and assures that they presenter is the holder. | # PEP = policy enforcement point accepts sources of attributes and assures that they presenter is the holder. | ||
Revision as of 19:20, 1 June 2022
Full Title or Meme
In this wiki the common therm for a Verifier is a Relying Party. The distinction seems to be moot.
Context
- This particular page is focused on entities called holders that have a collection of credentials that bind attributes to them and assures that the entity presenting them is the holder.
- The traditional name for an entity that needs validated data is a Relying Party. A Verifier may be a Relying Party or only a process that performs a function for one.
- Verification is the process for determining whether or not an applicant fulfills the requirements or specifications established - a definition derived from the MITRE Systems Engineering Guide.[1]
Problems
- The term Verifier could be limited to just the role played by any Entity in assuring that the data received meets its own criteria for acceptance.
- Some verticals, like finance and health, are highly regulated and typically require that their data controllers are certified for conformance with very restrictive regulations. Others have lighter regulation like the US Federal Trade commission.
- In all cases the verifier will be given a set of policies that they apply to Claimants seeking access. In a world where policies can change will little notice, it behooves the Verifier to create a Policy-Based Access Control applications that does not require reprogramming of the application to meet changing policies.
Solutions
For this wiki we break the Verifier into two roles from SAML:
- Holder = a real-world entity that has a collection of centennials in a digital format contained in a digital wallet.
- PDP = policy definition point may act as a Credential Aggregation process that accepts a collection of sources and produces a ticket for the holder that still needs to be bound to the person presenting the ticket.
- PEP = policy enforcement point accepts sources of attributes and assures that they presenter is the holder.