Native App
From MgmtWiki
Full Title or Meme
A digital Entity that is operating on a User Device, but is typically supplied by some App Store or some Federation. The term is typically used only with mobile user devices to distinguish it from a Progressive Web App.
Context
This page is an overview which is expanded on the wiki pages Native App Security and Native App Privacy.
- When discussing the use of the internet by a user, what is really meant is the Presence of the user operating an agent on an internet connection during some sort of Authentication process.
- From the time of the authentication with the agent forward, the user's Presence is seldom verified unless some individual action requires reconfirmation of the user's Presence, which may vary from a physical gesture on the screen to a test of some biological feature of the user.
- Typically the Native App will run on a User Device in the user's physical possession, but it is possible that the agent is running on a service in The Cloud.
- The Native App may act like a browser and supply an HTTP user agent string, but it should not be considered to be a User Agent.
- The Native App may act like a web server by registering Native App URI Handlers so that it will receive registered URLs entered into the browser.
- It is worth noting that a Progressive Web App (PWA) can be loaded into the browser and that there is some idea that it will eventually have all the capabilities of a Native App. This concept is hard to reconcile with the limited control of the security of the PWA.
This diagram from NIST shows the Native App embedded in the layers that go into creation of the user experience on a mobile device
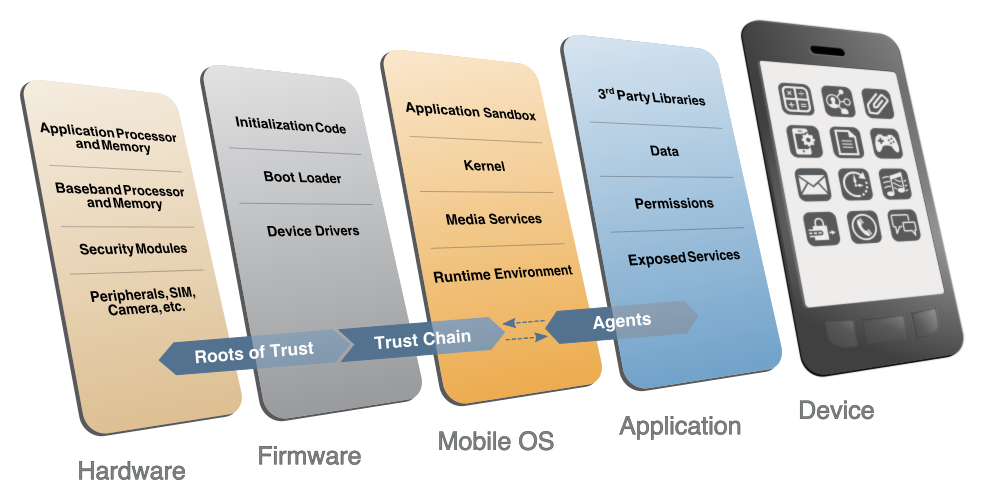
Problems
- Nearly any application running on a user's device is allowed to access the internet and claim that it represents the user. There is no built-in mechanism to test this assertion by an internet connected service. The internet was designed to connect computer systems, and that is all it can be relied upon to do.
- Any Web Site that wishes to create a Persistent Identifier for a User will need to take responsibility for any necessary Assurance that the Native App has not been compromised by an attacker.
- Most of the larger enterprises operating on The Web prefer to supply a Native App to the users device to improve the User Experience for that site.
- At of 2020-06 the uptake of Progressive Web Applications or Web Apps is increasing as it provides a better download experience for the user, but it is not able at this time to access the full functionality of the device, like the file system or the Trusted Execution Environment (TEE).
- To be sure that the User's intent is expressed by the Native App appears to be an insurmountable obstacle.
- Aners Rundgren's page describes some of the problems in more detail.
- Native App acceptance in the marketplace may, by itself, be a threat to the majority of users who cannot understand who to trust. A recent report[1] tells the story "When my mom fell victim to a phone scam, we learned a painful truth: The explosion of personal finance apps makes it all too easy to target vulnerable people."
Solutions
- Certification of the Native App please refer to page Native App Security.
- The Native App should perform all Authentication of the user by way of a browser (User Agent) selected by the user and running on the user's device using a trusted Identifier or Attribute Provider.
- Pre Oauth Entity Trust describes a means to represent third-party application endorsement for health care applications. POET’s goal is to help consumers distinguish between applications that have an endorsement versus applications that have no pedigree (i.e untrusted and could be malicious).
- Some sort of statement from the app developers about the app is required in the form of a manifest or Mobile Assurance Statement. (Note that the link will cause a download of the spec.)
References
- ↑ Becca Andrews They were calling to help, then they stole thousands Wired (2022-02-03) https://www.wired.com/story/phone-scam-phishing-finance-apps/
Other Materiel
- Native App Security page in this wiki
- Native App Privacy page in this wiki
- Native App URI Handlers page in this wiki
- Technology Acceptance page in this wiki
- W3C page on web apps best practices as of (2010-12-10).
- IETF RFC 8252 OAuth 2.0 for Native Apps https://tools.ietf.org/html/bcp212#section-7.2
- Apple App Store Review Guidelines https://developer.apple.com/app-store/review/guidelines/
- Apple building a trusted ecosystem for millions of apps.